Check that your User Rights Assignment policy settings comply with security standards in both your Group Policy Objects and on all your Windows computers at once with our reporting tool XIA Configuration.
Use the built-in Windows compliance benchmark to expose servers and workstations that do not meet your security policies.
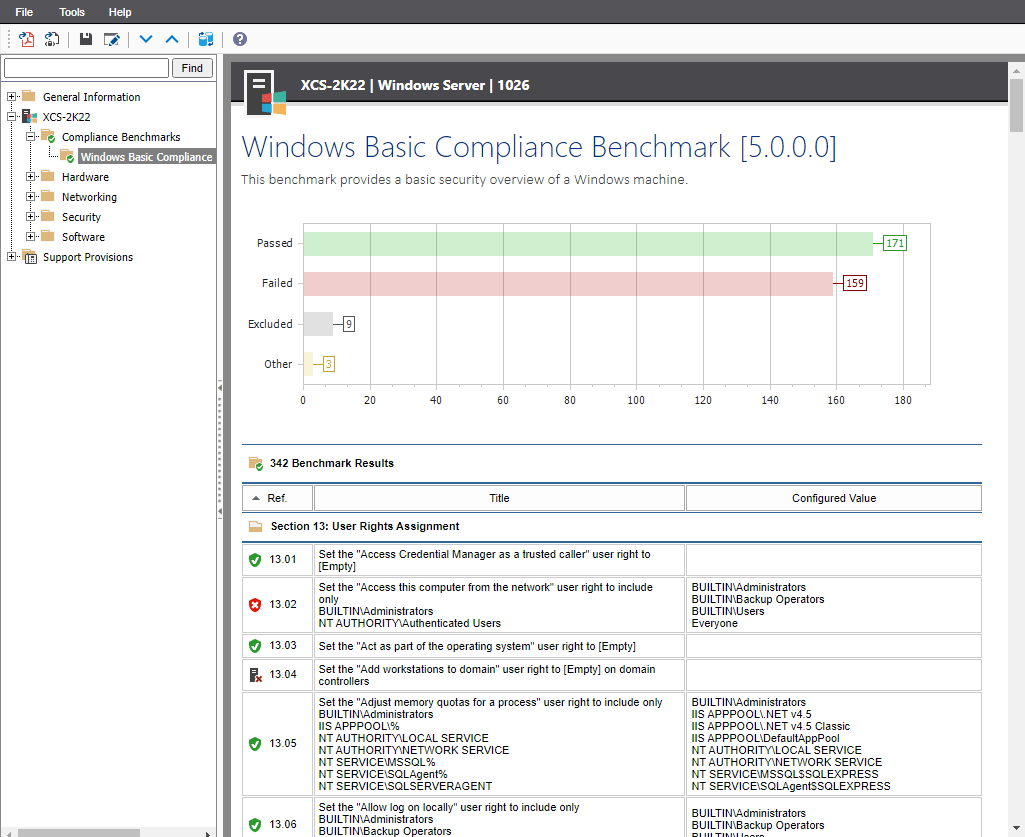 The Windows compliance benchmark tests your User Rights Assignment settings against recommended values
The Windows compliance benchmark tests your User Rights Assignment settings against recommended values
User Rights Assignment in Group Policy
User Rights Assignment policy settings are typically viewed in the Group Policy Management Console in the following section:
Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment
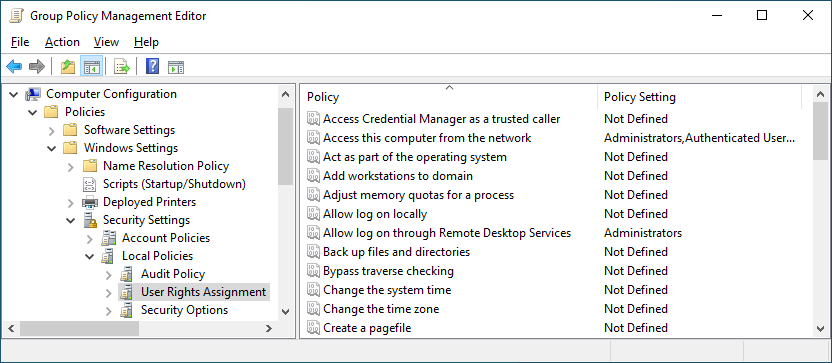 User Rights Assignment in the GPMC
User Rights Assignment in the GPMC
XIA Configuration presents this data in a modern, intuitive web interface and provides reporting functionality allowing you to audit all your Group Policy Objects at once.
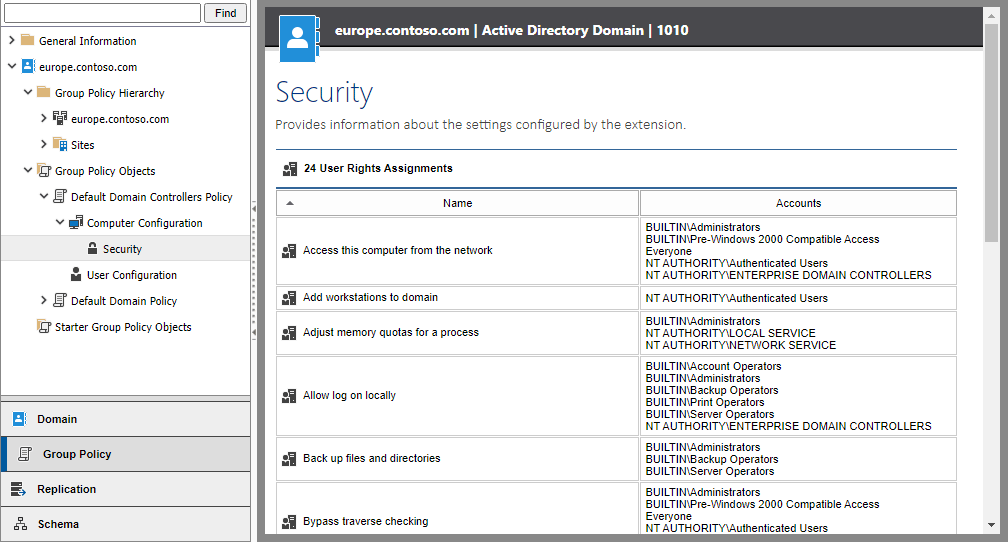 View User Rights Assignments in a modern web interface
View User Rights Assignments in a modern web interface
Audit and document your User Rights Assignment settings
If you're performing a security audit on your network, checking group policy settings is essential. As well as getting data from Group Policy, XIA Configuration also automates the retrieval of applied security settings across all your Windows computers.
- The reporting feature allows you to query all your computers at once
- The Windows compliance benchmark allows you to check your data complies with security standards
- Report filters allow you to get the data you need for external auditors
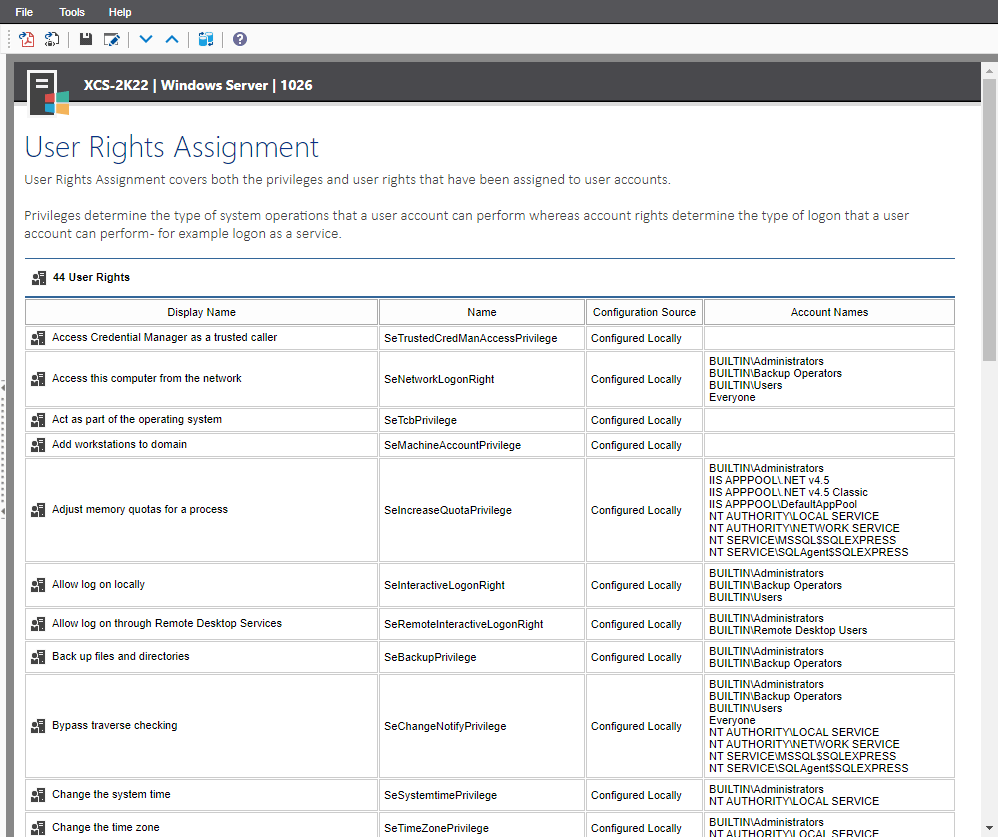 View your User Rights Assignment settings and configuration source
View your User Rights Assignment settings and configuration source
Check your User Rights Assignment security settings
Both the privileges and the user rights that have been assigned to user accounts are covered.
- Display name - for example "Access to this computer from the network"
- Internal right or privilege name - for example "SeNetworkLogonRight"
- Configuration Source (Local / Group Policy (GPO))
- Users and groups with this right assigned
Press the Show details link to view all the user rights retrieved by XIA Configuration.
Show details
- Access Credential Manager as a trusted caller
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow log on through Remote Desktop Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Change the time zone
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Create symbolic links
- Debug programs
- Deny access to this computer from the network
- Deny log on as a batch job
- Deny log on as a service
- Deny log on locally
- Deny log on through Remote Desktop Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase a process working set
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify an object label
- Modify firmware environment values
- Obtain an impersonation token for another user in the same session
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process-level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files or other objects
Try auditing your user rights assignment settings for free